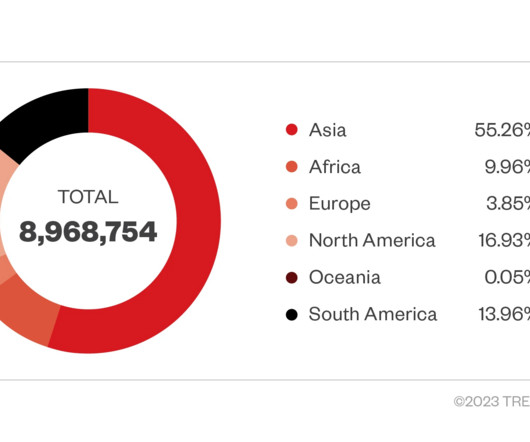
Lemon Group gang pre-infected 9 million Android devices for fraudulent activities
Security Affairs
MAY 19, 2023
The experts discovered a system library called libandroid_runtime.so that was tampered to inject a snippet code into a function called println_native. Then the injected code will decrypt a DEX file from the data section and load it into memory. The function is called when the print logs. ” continues the report.











Let's personalize your content