PseudoManuscrypt, a mysterious massive cyber espionage campaign
Security Affairs
DECEMBER 16, 2021
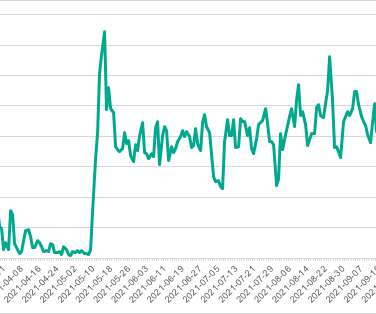
of all systems targeted by the PseudoManuscrypt malware are part of industrial control systems (ICS) used by organizations in multiple industries, including Engineering, Building Automation, Energy, Manufacturing, Construction, Utilities, and Water Management. The experts revealed that at least 7.2%












Let's personalize your content