XDSpy APT remained undetected since at least 2011
Security Affairs
OCTOBER 2, 2020
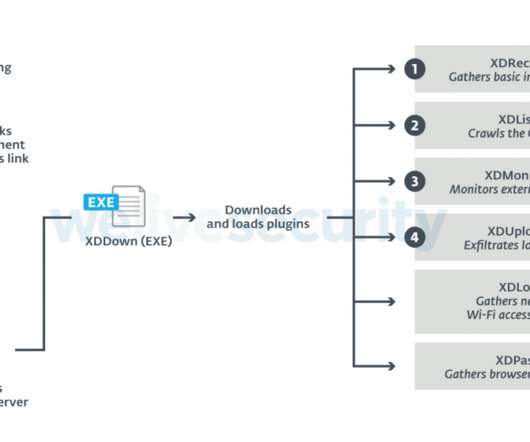
The APT group, recently discovered by ESET, targeted government and private companies in Belarus, Moldova, Russia, Serbia, and Ukraine, including militaries and Ministries of Foreign Affairs. “It is very uncommon to find a cyber espionage operation without any public reporting after almost 10 years of activity.”














Let's personalize your content