Targeted operation against Ukraine exploited 7-year-old MS Office bug
Security Affairs
APRIL 28, 2024
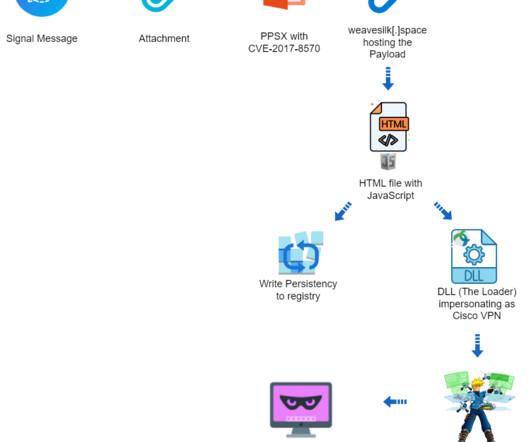
The payload includes a dynamic-link library (vpn.sessings) that injects the post-exploitation tool Cobalt Strike Beacon into memory and awaits commands from the C2 server. The DLL also implements features to evade detection and avoid analysis by security experts. Threat actors used a cracked version of Cobalt Strike.



















Let's personalize your content