China-linked Moshen Dragon abuses security software to sideload malware
Security Affairs
MAY 3, 2022
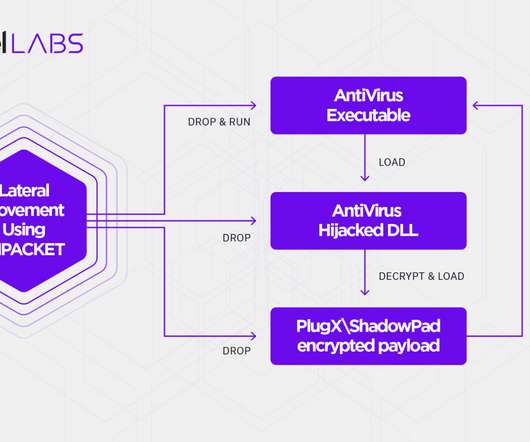
RedFoxtrot has been active since at least 2014 and focused on gathering military intelligence from neighboring countries, it is suspected to work under the PLA China-linked Unit 69010. The threat actor systematically utilized software distributed by security vendors to sideload ShadowPad and PlugX variants.” Pierluigi Paganini.



























Let's personalize your content