Iranian hackers access unsecured HMI at Israeli Water Facility
Security Affairs
DECEMBER 4, 2020
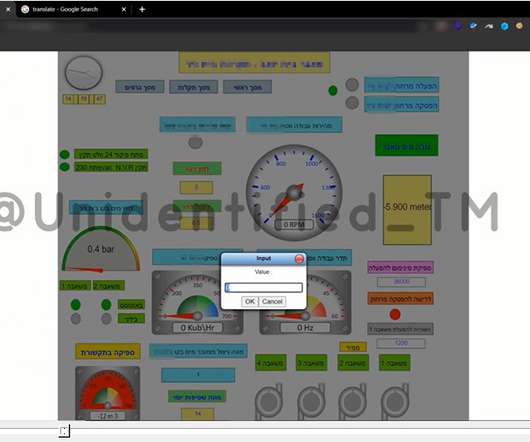
Furthermore, at the time of the publication, the system did not use any authentication method upon access.” ” reads the blog post published by OTORIO. Experts noticed that the system still allows communications on port 502, which is used for Modbus protocol, that doesn’t require any authentication/encryption.













Let's personalize your content