eIDAS 2.0 REGULATION WILL CHANGE IDP USE CASES INCLUDING ID CAPTURE IN THE EU
Info Source
JULY 18, 2023
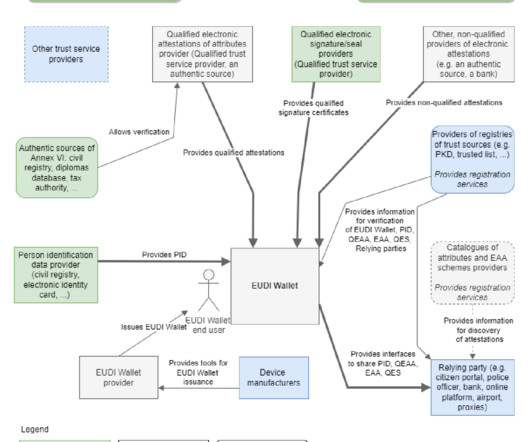
The expanded regulation has far reaching implications for software vendors, service providers and public and private organisations with a focus on Government to Consumer (G2C) and Business to Consumer (B2C) end customers. Some business applications primarily involve Capturing ID, e.g., hospitality or access restrictions.












Let's personalize your content