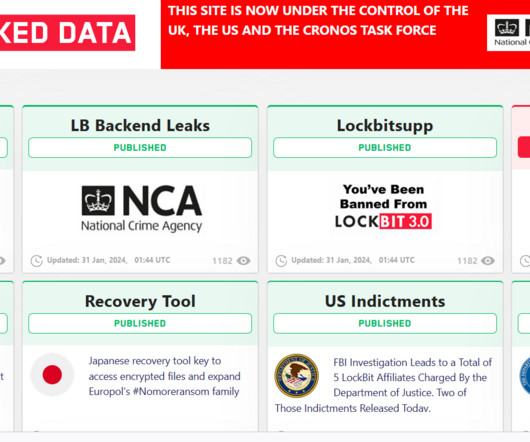
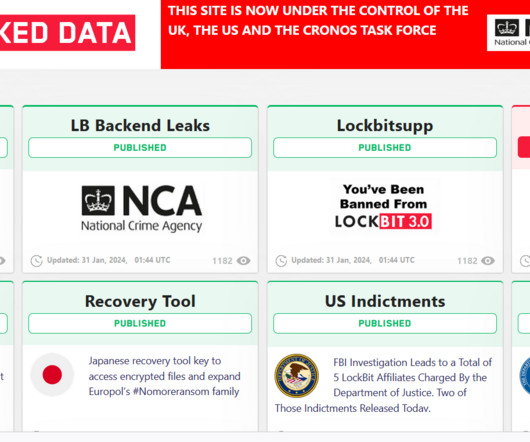
US GOV OFFERS A REWARD OF UP TO $15M FOR INFO ON LOCKBIT GANG MEMBERS AND AFFILIATES
Security Affairs
FEBRUARY 21, 2024
Law enforcement also had access to data stolen from the victims of the ransomware operation, a circumstance that highlights the fact that even when a ransom is paid, the ransomware gang often fails to delete the stolen information. In 2022, LockBit was one of the most active ransomware groups, and its prevalence continued into 2023.














Let's personalize your content