INSIGHTS from SENTINEL
Thales Cloud Protection & Licensing
JUNE 23, 2021
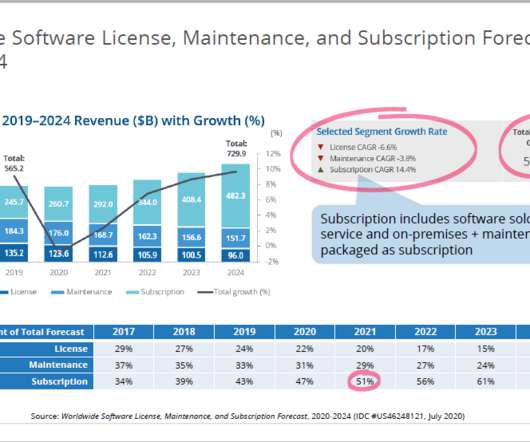
Presented by Mark Thomason, IDC Research Director. ?Which The subscription model also lets you optimize product utilization so that you can segment your offering and demonstrate the true value of your product. Images credit: IDC presentation, Where Companies Fail and How to Avoid the Traps of Shifting to Subscriptions June 2021. .











Let's personalize your content