Expert found 1,236 websites infected with Magecart e-skimmer
Security Affairs
MAY 13, 2020
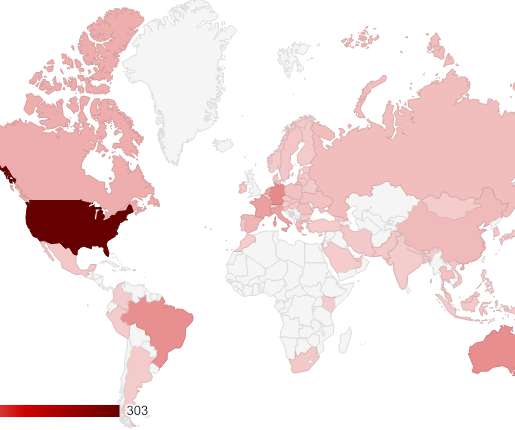
A security researcher is warning of a new wave of MageCart attackers, he has found over 1,000 domains infected with e-skimmers. MageCart gangs continue to be very active, security researcher Max Kersten discovered 1,236 domains hosting e-skimmer software. This addition is considered out of scope for this research.”
















Let's personalize your content