Winnti APT Group targeted Hong Kong Universities
Security Affairs
FEBRUARY 1, 2020
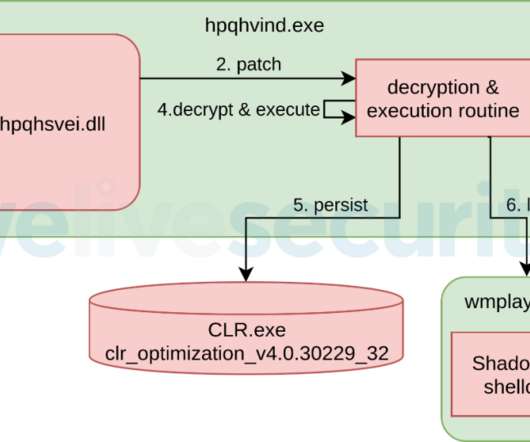
” The Winnti group was first spotted by Kaspersky in 2013, but according to the researchers the gang has been active since 2007. “In contrast, the variants we described in our white paper didn’t even have that module embedded.” ” continues the report.















Let's personalize your content