Apache Log4j Zero Day Exploit Puts Large Number of Servers at Severe Risk
eSecurity Planet
DECEMBER 10, 2021
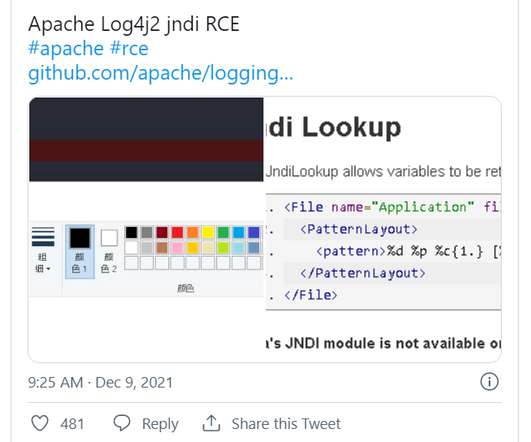
A critical vulnerability in the open-source logging software Apache Log4j 2 is fueling a chaotic race in the cybersecurity world, with the Apache Software Foundation (ASF) issuing an emergency security update as bad actors searched for vulnerable servers. release of Log4j 2 that fixes the RCE vulnerability.

















Let's personalize your content