New Golang-based Crypto worm infects Windows and Linux servers
Security Affairs
DECEMBER 31, 2020
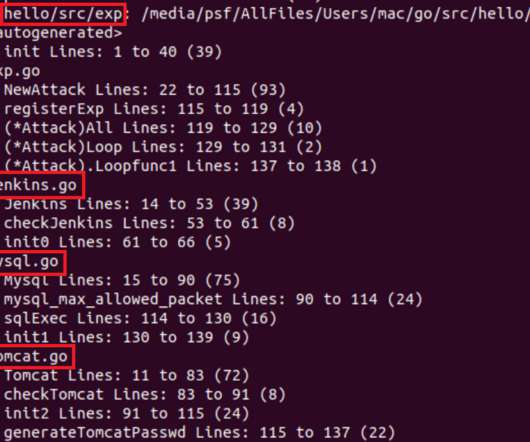
Experts pointed out that an older version of the worm also attempted to exploit CVE-2020-14882 WebLogic’s vulnerability. Experts pointed out that an older version of the worm also attempted to exploit CVE-2020-14882 WebLogic’s vulnerability. The threat actors behind this campaign have been actively updating the malicious code.
















Let's personalize your content