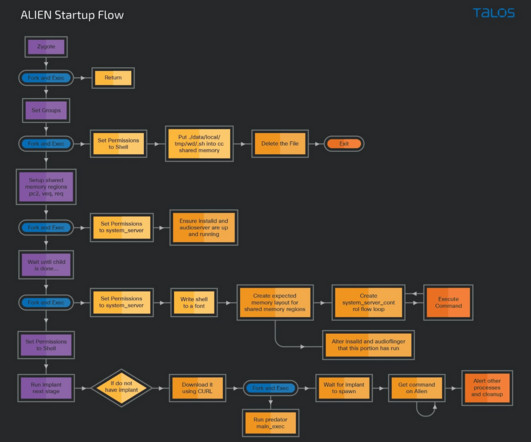
Researchers analyzed the PREDATOR spyware and its loader Alien
Security Affairs
MAY 29, 2023
Both components work together to bypass traditional security features on the Android operating system. ” In May 2022, Google’s Threat Analysis Group (TAG) researchers discovered three campaigns, between August and October 2021, targeting Android users with five zero-day vulnerabilities.















Let's personalize your content