How to Perform a Content Migration - Your Checklist for Success
AIIM
DECEMBER 19, 2019
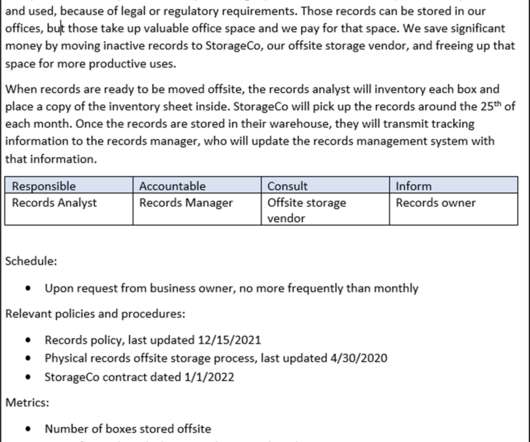
The source and target system administrators should be involved as well. This phase would include the following steps: Take Inventory of the Source System: This means identifying the information in the system, its metadata, how it is categorized and classified, any relevant business rules or workflows, security settings, etc.












Let's personalize your content