How to secure QNAP NAS devices? The vendor’s instructions
Security Affairs
JANUARY 7, 2022
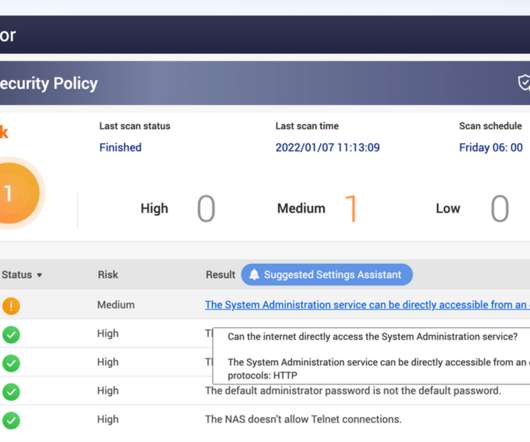
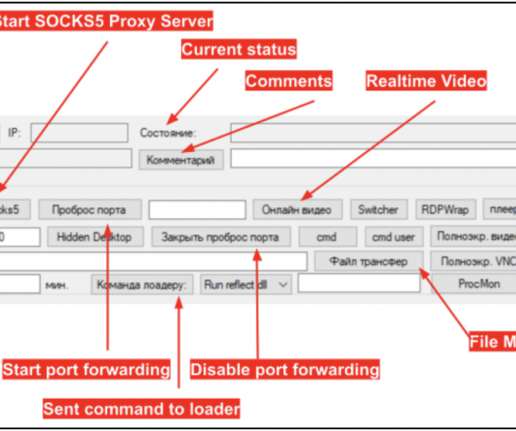
If the NAS is exposed to the Internet the dashboard will display the message “The System Administration service can be directly accessible from an external IP address via the following protocols: HTTP.”. Administrator of devices exposed to the Internet should: Disable the Port Forwarding function of the router.







































Let's personalize your content