Cable Haunt flaw exposes 200M+ Broadcom-based cable modems at remote hijacking
Security Affairs
JANUARY 10, 2020
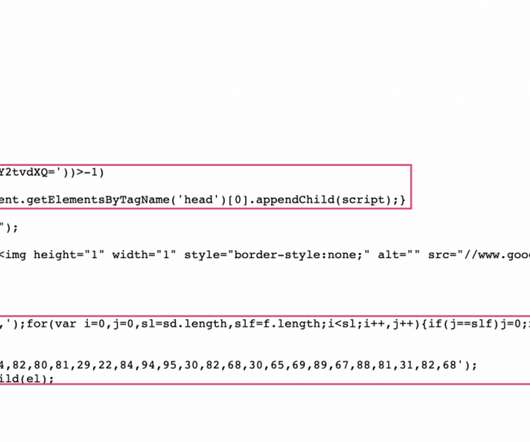
The reason for this is that the vulnerability originated in reference software, which has seemingly been copied by different cable modems manufacturers when creating their cable modem firmware. Secondly the vulnerable endpoint is hit with a buffer overflow attack, which gives the attacker control of the modem.”














Let's personalize your content