Compal, the Taiwanese giant laptop manufacturer hit by ransomware
Security Affairs
NOVEMBER 9, 2020
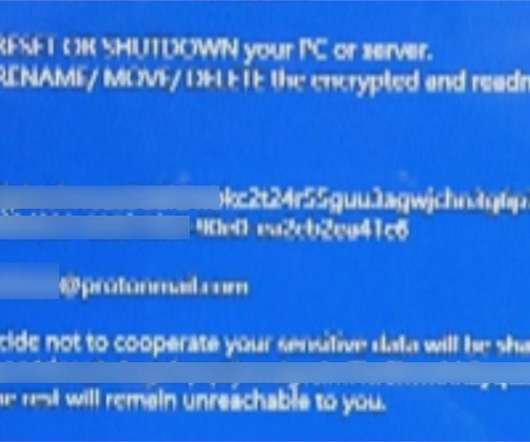
The Taiwanese electronics manufacture Compal suffered a ransomware attack over the weekend, media blames the DoppelPaymer ransomware gang. It is the second-largest contract laptop manufacturer in the world behind Quanta Computer. Acer, Lenovo, Dell, Toshiba, Hewlett-Packard and Fujitsu. It also licenses brands of its clients.














































Let's personalize your content