CERT-UA warns of a phishing campaign targeting government entities
Security Affairs
AUGUST 13, 2024
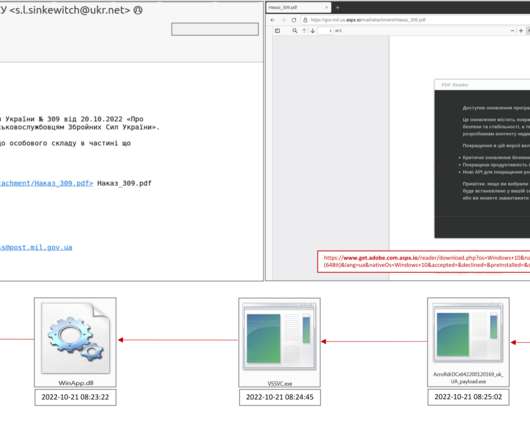
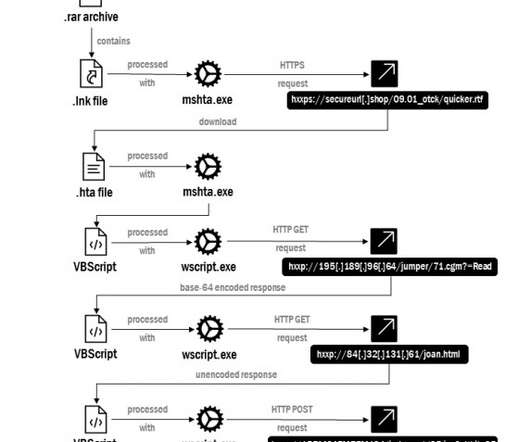
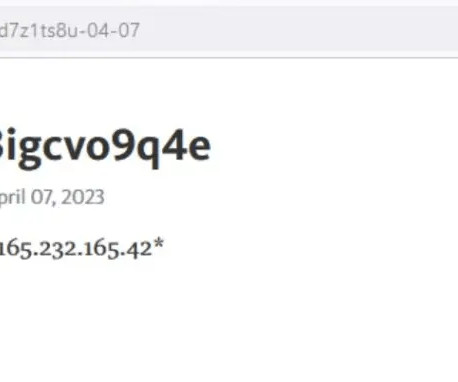
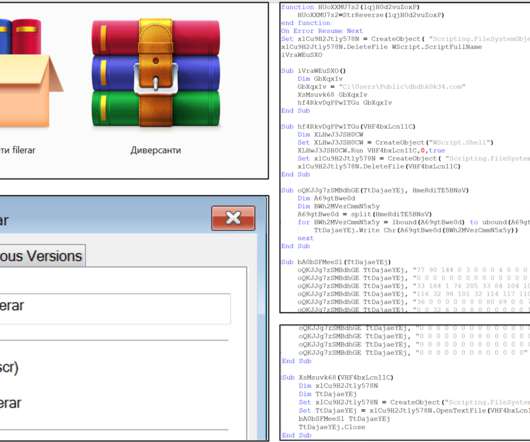
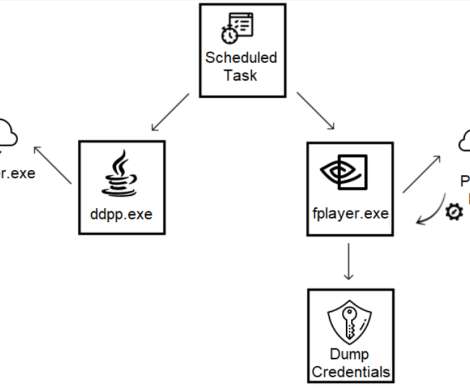
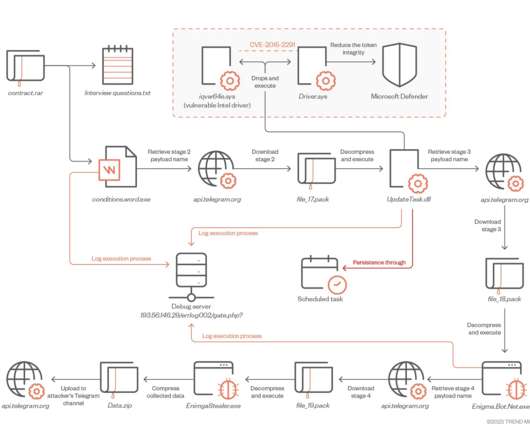
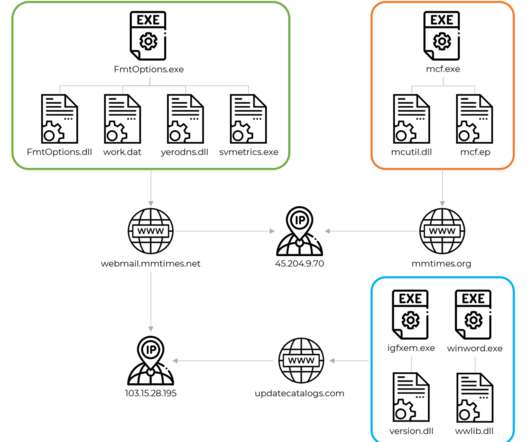
CERT-UA warned that Russia-linked actor is impersonating the Security Service of Ukraine (SSU) in a new phishing campaign to distribute malware. The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new phishing campaign targeting organizations in the country, including government entities.




































Let's personalize your content