Why Data Visibility is Important for Security
Thales Cloud Protection & Licensing
MARCH 16, 2021
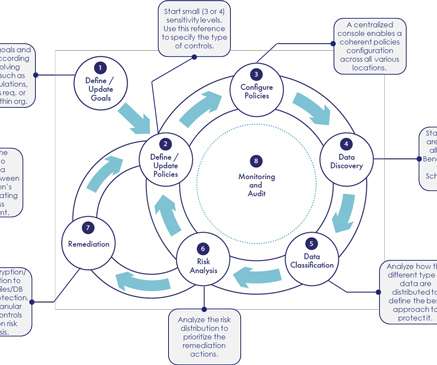
These numbers raise an important question, how should organizations coordinate their efforts to have in place effective security strategies? Knowing the data an organization handles allows defining holistic strategies focused on it. The data visibility process is not a one-time event. Identity & Access Management.















Let's personalize your content