Group-IB detects a series of ransomware attacks by OldGremlin
Security Affairs
SEPTEMBER 23, 2020
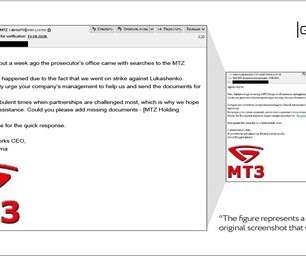
Since March, the attackers have been trying to conduct multistage attacks on large corporate networks of medical labs, banks, manufacturers, and software developers in Russia. The operators use a suite of custom tools with the ultimate goal of encrypting files in the infected system and holding it for a ransom of about $50,000.











Let's personalize your content