UK newspaper The Telegraph exposed a 10TB database with subscriber data
Security Affairs
OCTOBER 5, 2021
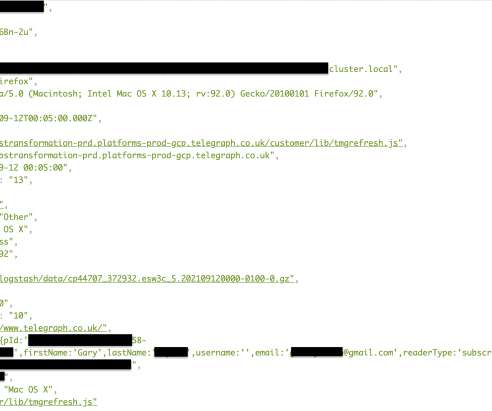
The data was stored on an exposed Elasticsearch cluster, most of the data were encrypted, but personal details of at least 1,200 Telegraph subscribers and registrants were in clear test along with a a huge trove of internal server logs. The database also included some Apple news subscribers or registrants’ passwords.





















Let's personalize your content