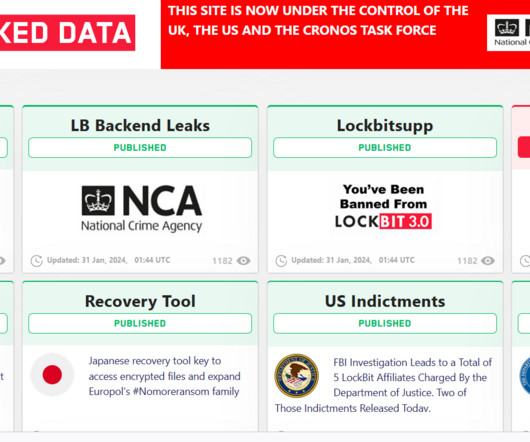
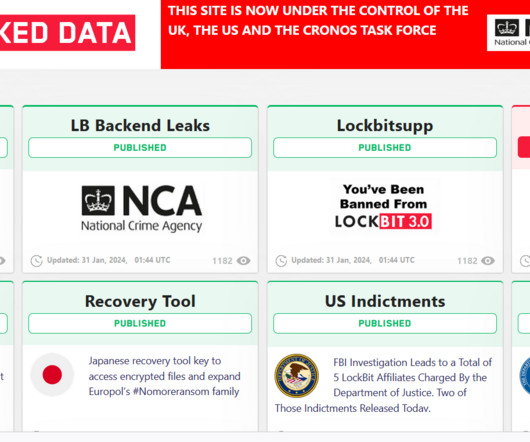
US GOV OFFERS A REWARD OF UP TO $15M FOR INFO ON LOCKBIT GANG MEMBERS AND AFFILIATES
Security Affairs
FEBRUARY 21, 2024
government offers rewards of up to $15 million for information that could lead to the identification or location of LockBit ransomware gang members and affiliates. LockBit is a prominent ransomware operation that first emerged in September 2019. ” reads the press release published by the U.S. reads the NCA’s announcement. “The















Let's personalize your content