Avast released a free decryptor for the Windows version of the Akira ransomware
Security Affairs
JULY 1, 2023
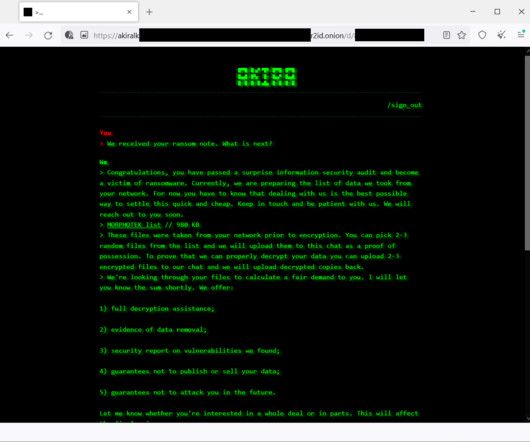
This Linux version is 64-bit and also uses the Boost library, it uses the Crypto++ library instead of Windows CryptoAPI. “During the run, the ransomware generates a symmetric encryption key using CryptGenRandom() , which is the random number generator implemented by Windows CryptoAPI. Bernstein’s implementation ).”

















Let's personalize your content