Cops Will Be Able to Scan Your Fingerprints With a Phone
WIRED Threat Level
JUNE 17, 2022
Contactless fingerprinting uses a smartphone camera to capture your prints—and opens up a whole new set of privacy concerns.

WIRED Threat Level
JUNE 17, 2022
Contactless fingerprinting uses a smartphone camera to capture your prints—and opens up a whole new set of privacy concerns.

Data Breach Today
JUNE 17, 2022
DXC Technology's Michael Baker on Top Threats, Recruitment Tips, Career Advice Threat watch: The ongoing Russia-Ukraine war continues to pose both direct and indirect risks to enterprise networks, says Michael Baker, vice president and IT CISO of IT services and consulting firm DXC Technology. He also discusses recruiting and retaining new talent.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
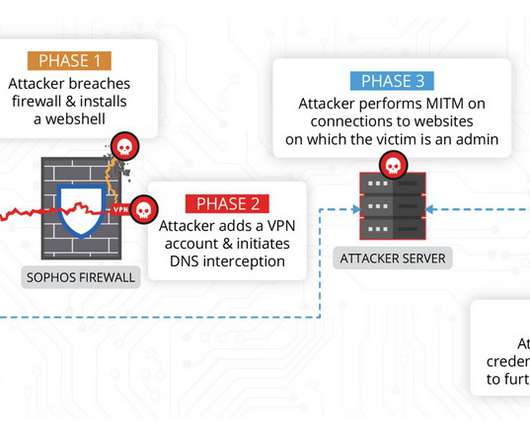
Security Affairs
JUNE 17, 2022
China-linked threat actors exploited the zero-day flaw CVE-2022-1040 in Sophos Firewall weeks before it was fixed by the security vendor. Volexity researchers discovered that the zero-day vulnerability, tracked as CVE-2022-1040 , in Sophos Firewall was exploited by Chinese threat actors to compromise a company and cloud-hosted web servers it was operating.

Data Breach Today
JUNE 17, 2022
The State of Passwordless in 2022, New Identity Technologies In the latest weekly update, Jeremy Grant, coordinator of the Better Identity Coalition, joins three editors at ISMG to discuss important cybersecurity issues, including where we are with passwordless, if we are getting closer to a U.S. federal privacy law, and next-gen authentication technologies.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Schneier on Security
JUNE 17, 2022
We’ve always known that phones—and the people carrying them—can be uniquely identified from their Bluetooth signatures, and that we need security techniques to prevent that. This new research shows that that’s not enough. Computer scientists at the University of California San Diego proved in a study published May 24 that minute imperfections in phones caused during manufacturing create a unique Bluetooth beacon , one that establishes a digital signature or fingerprint di
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Data Matters
JUNE 17, 2022
Hattie Davison, UK Government, Department for Digital, Culture, Media and Sport, Head of Data Reform Policy. The post Spotlight on Women in Privacy – Hattie Davison appeared first on Data Matters Privacy Blog.
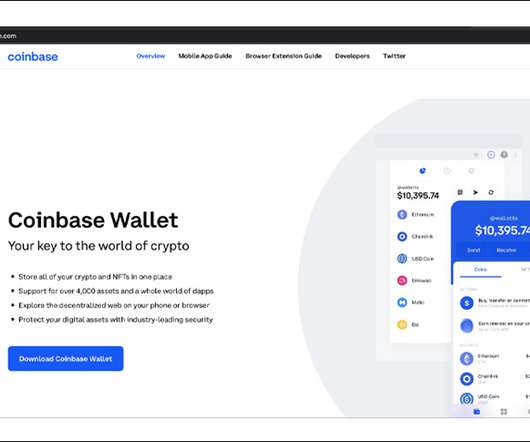
Data Breach Today
JUNE 17, 2022
Backdoored Apps Allow Normal Functioning of Wallet While Exfiltrating Master Key A "technically sophisticated" threat campaign is cloning cryptocurrency apps to steal funds from web3 wallet users, security researchers at Confiant say. The campaign, dubbed SeaFlower, uses cloned wallet apps offered by MetaMask, Coinbase, imToken and TokenPocket to carry out the theft.

Collibra
JUNE 17, 2022
The son of Jamaican parents, Nathaniel Cooper was born and raised in New Jersey, USA. When it was time for college, he chose one of the most prestigious HBCU’s (Historical Black College & University) to attend, Howard University. . “Black people are so often stereotyped and being at Howard University opened my mind to the black diaspora and the many contributions to society that Black intellectuals have made around the world.

Data Breach Today
JUNE 17, 2022
SentinelOne President Nick Warner on How Attivo and Scalyr Advanced the XDR Mission SentinelOne has expanded its detection and response capabilities beyond the endpoint in recent years with the acquisition of data analytics tech developer Scalyr and identity and deception technology vendor Attivo Networks, says Nicholas Warner, president of security.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Dark Reading
JUNE 17, 2022
Most of the attacks involve the use of automated exploits, security vendor says.

Data Breach Today
JUNE 17, 2022
Lawmakers Impatient With Hands-Off Approach to Industry Cybersecurity Practices A bipartisan U.S. proposal for a national privacy law also imposes new cybersecurity regulatory mandates onto the private sector. The inclusion of a data security section in draft privacy legislation shows the Washington consensus for voluntary industry measures is wearing thin.
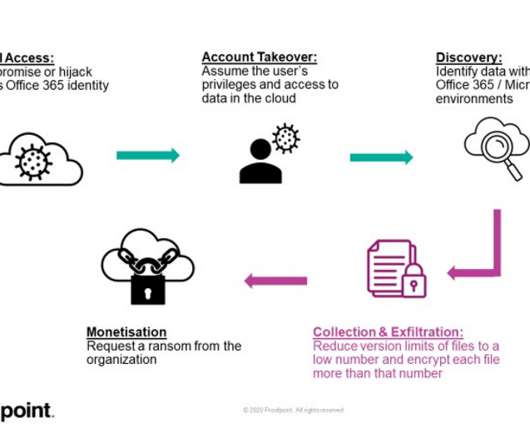
Security Affairs
JUNE 17, 2022
Experts discovered a feature in Microsoft 365 suite that could be abused to encrypt files stored on SharePoint and OneDrive and target cloud infrastructure. Researchers from Proofpoint reported that a feature in the in Microsoft 365 suite could be abused to encrypt files stored on SharePoint and OneDrive. “Proofpoint has discovered a potentially dangerous piece of functionality in Office 365 or Microsoft 365 that allows ransomware to encrypt files stored on SharePoint and OneDrive in a way

Data Breach Today
JUNE 17, 2022
Okta's Sean Frazier on Securing the Supply Chain, Software Development Life Cycle Interest in passwordless authentication architecture continues to grow among U.S. government agencies and departments as they embrace more modern approaches to identity and access management, says Sean Frazier, federal chief security officer at Okta.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Dark Reading
JUNE 17, 2022
The energy sector remains susceptible to both espionage between nation-states and cybercrime, and recent developments keep pointing toward more attacks.

Data Breach Today
JUNE 17, 2022
SecurityScorecard CEO Aleksandr Yampolskiy on Why This War Is Personal The war between Russia and Ukraine isn't an abstract concern for SecurityScorecard CEO Aleksandr Yampolskiy. It's a deeply personal one since Yampolskiy, who is now a U.S. citizen, grew up in Russia and rode the train to Ukraine every summer to visit his grandmother.

Dark Reading
JUNE 17, 2022
The QNAP network-connected devices, used to store video surveillance footage, are a juicy target for attackers, experts warn.

Data Breach Today
JUNE 17, 2022
Contrast Security CPO Steve Wilson on Why Log4j Hack Is a Sign of Things to Come The discovery and subsequent exploitation of a critical zero-day vulnerability in Apache's Log4j open-source library has highlighted the importance of code security in today's threat landscape, according to Contrast Security Chief Product Officer Steve Wilson.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Security Affairs
JUNE 17, 2022
Experts uncovered an enterprise-grade surveillance malware dubbed Hermit used to target individuals in Kazakhstan, Syria, and Italy since 2019. Lookout Threat Lab researchers uncovered enterprise-grade Android surveillance spyware, named Hermit, used by the government of Kazakhstan to track individuals within the country. The latest samples of this spyware were detected by the researchers in April 2022, four months after a series of nation-wide protests against government policies that were viol

Dark Reading
JUNE 17, 2022
The code injection vulnerability is being actively exploited in the wild, researchers say.

Threatpost
JUNE 17, 2022
Evidence suggests that a just-discovered APT has been active since 2013.

Dark Reading
JUNE 17, 2022
Security teams — who are already fighting off malware challenges — are also facing renewed attacks on cloud assets and remote systems.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

WIRED Threat Level
JUNE 17, 2022
Despite major progress fighting spam and scams, the roots of the problem go far deeper than your phone company’s defenses.

OpenText Information Management
JUNE 17, 2022
One of the most striking facts about the ‘Great Resignation’ is just how many people are willing to walk out of their current job with nowhere else to go. Workers are no longer willing to settle for poor experiences simply to guarantee an income. As people search for more fulfilling roles and career paths, companies … The post Focus on employee experiences to master modern work appeared first on OpenText Blogs.

IG Guru
JUNE 17, 2022
Check out their post here. The post ACEDS writes about the new Information Governance ISO Standard appeared first on IG GURU.

OpenText Information Management
JUNE 17, 2022
Remote and hybrid work environments are here to stay and as corporate legal teams begin to reassess their needs in a post-pandemic environment, they are uniformly looking for ways to improve their prospects and transform their eDiscovery practices. The volumes of litigation, investigations and regulatory compliance matters continue to increase while data privacy regulations, cybersecurity … The post Support eDiscovery at scale to master modern work appeared first on OpenText Blogs.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Dark Reading
JUNE 17, 2022
The stakes are high when protecting CNI from destructive malware and other threats.

OpenText Information Management
JUNE 17, 2022
Collaboration in a trustworthy and reliable information management process is paramount to the future of work. New regulatory and privacy requirements continue to emerge as new content-sharing technology and hybrid work models pose new security and privacy challenges. With a highly distributed workforce, the information they need must find them, not create new opportunities for … The post Master modern work with stronger information protection appeared first on OpenText Blogs.

WIRED Threat Level
JUNE 17, 2022
The WikiLeaks founder will appeal the UK Home Office's decision to extradite him to the US.
Let's personalize your content