Spear-Phishing Campaign Uses COVID-19 to Spread LokiBot
Data Breach Today
APRIL 4, 2020
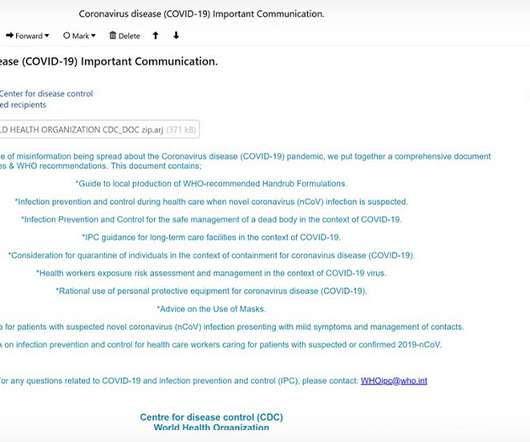
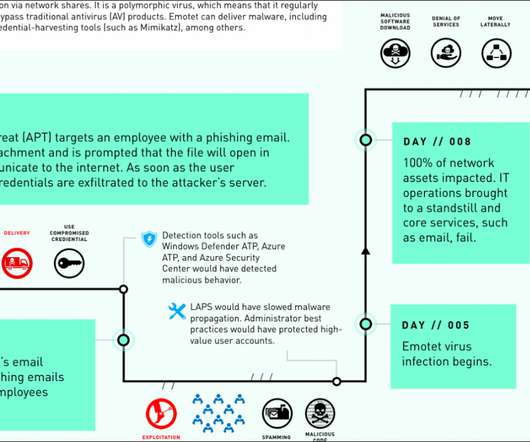
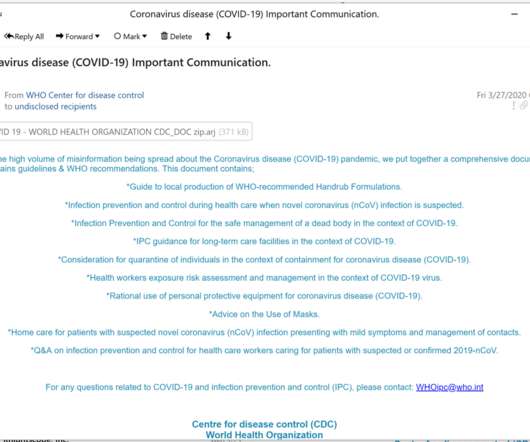
FortiGuard Labs Researchers Find WHO Images Used As Lure Again A recently uncovered spear-phishing campaign is using fears of the COVID-19 pandemic to spread an information stealer called LokiBot. FortiGuard Labs researchers find that cybercriminals are once again using WHO images as a lure.














Let's personalize your content