US Warns: Hackers Chaining Zerologon, Other Vulnerabilities
Data Breach Today
OCTOBER 10, 2020
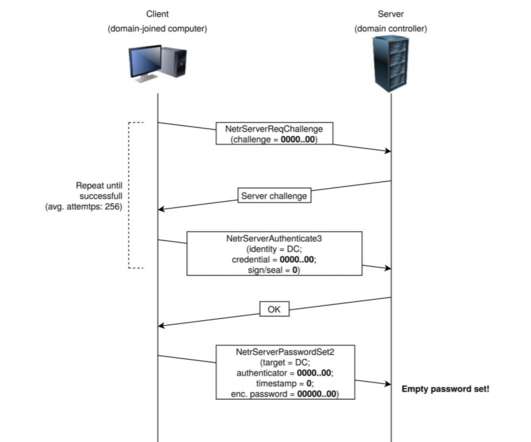
CISA Says APTs Gained Access to State and Local Election Support Systems CISA is warning that sophisticated hacking groups are chaining vulnerabilities together, such as the recent Zerologon bug along with other flaws, to target state and local government networks. In some cases, attackers gained access to election support systems.
















Let's personalize your content