Police Bust Suspected Ransomware Group Ringleader in Ukraine
Data Breach Today
NOVEMBER 28, 2023
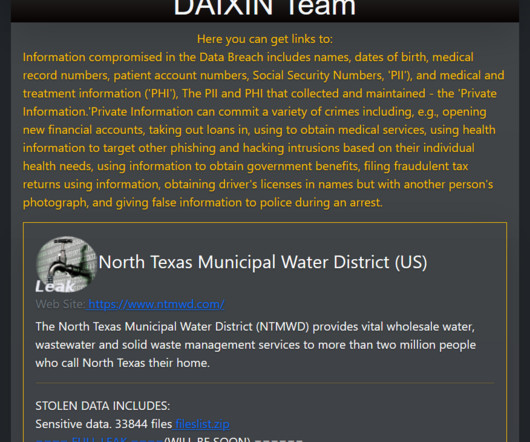
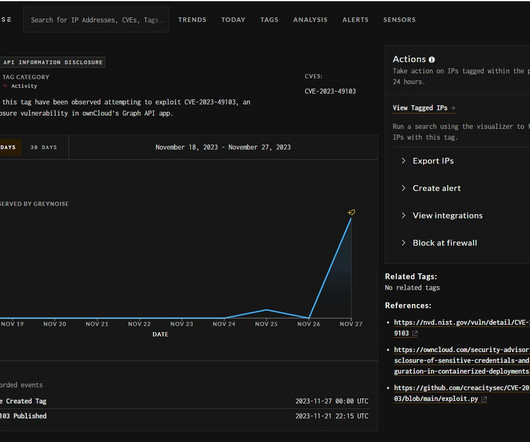
5 Suspects Arrested; Group Tied to Ransomware Attacks Against 1,800 Victims Police have arrested a group of criminals in Ukraine, including their alleged ringleader, who they suspect launched ransomware attacks against organizations across 71 countries, amassing at least 1,800 victims, from which they demanded ransoms collectively worth hundreds of millions of dollars.








































Let's personalize your content