Group Health Cooperative data breach impacted 530,000 individuals
Security Affairs
APRIL 10, 2024
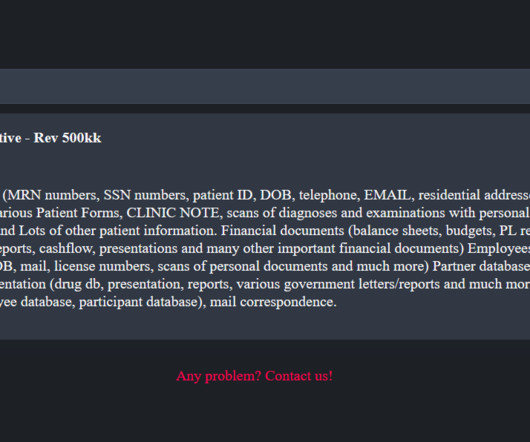
The Group Health Cooperative of South Central Wisconsin (GHC-SCW) is a non-profit organization that provides health insurance and medical care services to its members in the Madison metropolitan area of Wisconsin. “The attacker attempted to encrypt GHC-SCW’s system but was unsuccessful.”













Let's personalize your content