LockBit ransomware group claims to have hacked Bridgestone Americas
Security Affairs
MARCH 13, 2022
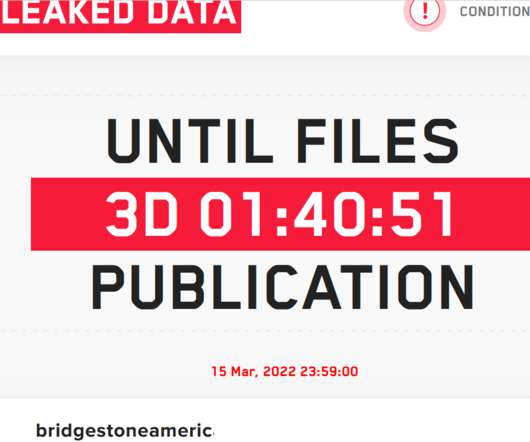
LockBit ransomware gang claimed to have hacked Bridgestone Americas, one of the largest manufacturers of tires. LockBit ransomware gang claimed to have compromised the network of Bridgestone Americas, one of the largest manufacturers of tires, and stolen data from the company.














Let's personalize your content