DarkHotel APT uses VPN zero-day in attacks on Chinese government agencies
Security Affairs
APRIL 6, 2020
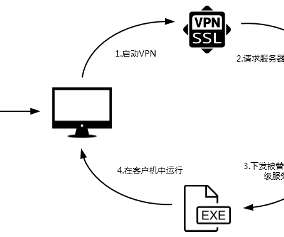
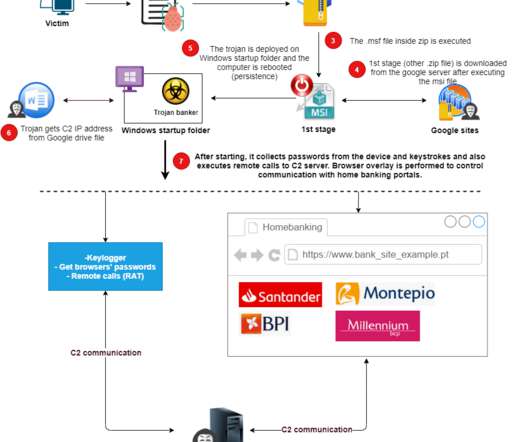
Chinese security-firm Qihoo 360 has uncovered a hacking campaign conducted by a DarkHotel APT group (APT-C-06) aimed at Chinese government agencies in Beijing and Shanghai. “Recently, Qihoo 360 captured malicious samples issued through hijacked security services of a domestic VPN vendor SangFor. are vulnerable.















Let's personalize your content