Enterprise Secrets Management Explained: Best Practices, Challenges, and Tool Selection
Thales Cloud Protection & Licensing
AUGUST 16, 2023
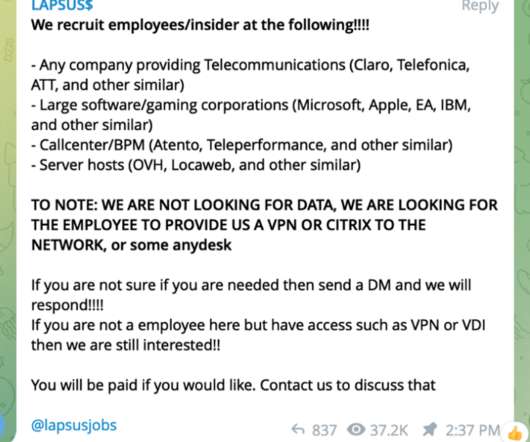
These secrets control data access when transferred between applications—sending information from a webpage, making a secure request to an API, accessing a cloud database, or countless other cases that modern enterprises encounter while pursuing digital transformation and increasing automation. What is secrets management?
















Let's personalize your content