How 5G Operators Can Prepare for The Quantum Era
Thales Cloud Protection & Licensing
JANUARY 29, 2024
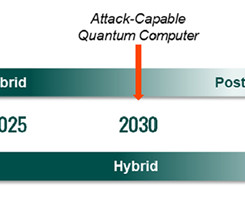
How 5G Operators Can Prepare for The Quantum Era madhav Tue, 01/30/2024 - 05:25 The Quantum State of Play in 5G Quantum computing has found theoretical application in modern computation systems, including cellular networks like 5G. However, many of these protocols are at risk due to their vulnerability to quantum attacks.














Let's personalize your content