Cybersecurity, why a hotline number could be important?
Security Affairs
OCTOBER 6, 2023
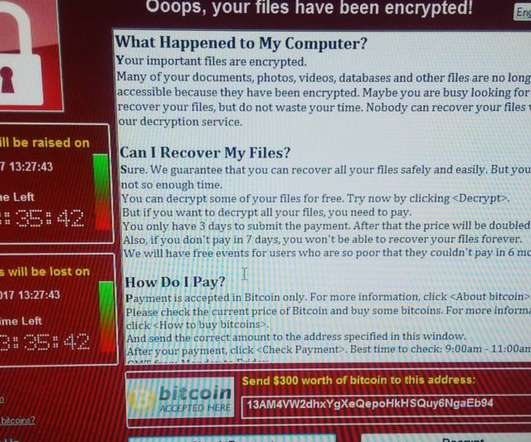
While the phone number for physical emergencies is already time-tested, the absence of a similar hotline for cybercrimes is a significant gap in our digital security. Statistics show a steady increase in cyber attacks targeting citizens and businesses, causing financial, security and privacy damage.
























Let's personalize your content