Identity Thieves Bypassed Experian Security to View Credit Reports
Krebs on Security
JANUARY 9, 2023
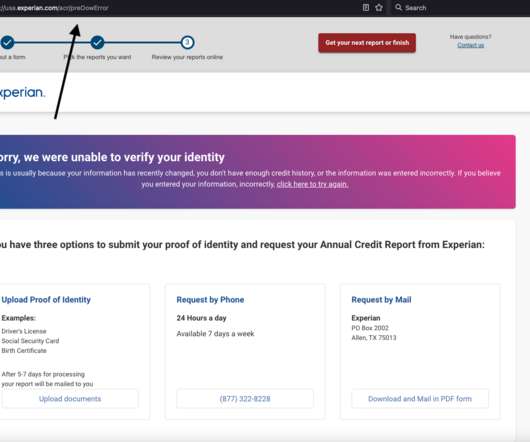
For example, there were four phone numbers on my Experian credit file: Only one of them was mine, and that one hasn’t been mine for ages. The report contains so many errors that it’s probably going to take a good deal of effort on my part to straighten out. Please don’t confuse a credit freeze (a.k.a.










Let's personalize your content