New Pro-Ocean crypto-miner targets Apache ActiveMQ, Oracle WebLogic, and Redis installs
Security Affairs
JANUARY 31, 2021
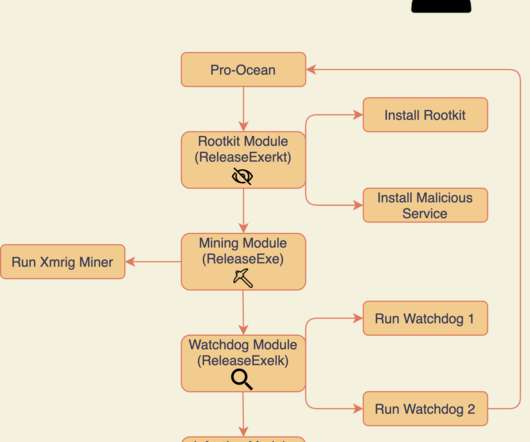
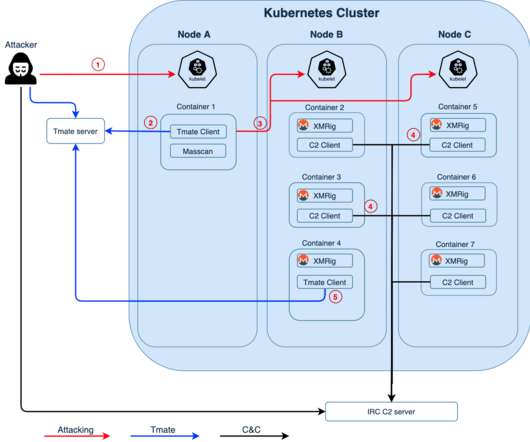
The Rocke group is using a new piece of cryptojacking malware dubbed Pro-Ocean to target Apache ActiveMQ, Oracle WebLogic, and Redis installs. The cybercrime group Rocke is using a new piece of cryptojacking malware called Pro-Ocean to target vulnerable Apache ActiveMQ, Oracle WebLogic, and Redis intalls.














Let's personalize your content