Doki, an undetectable Linux backdoor targets Docker Servers
Security Affairs
JULY 29, 2020
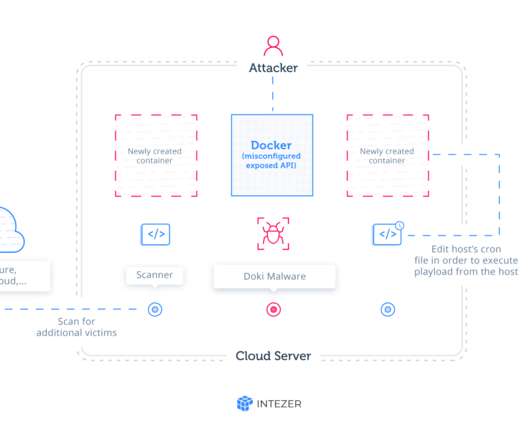
The ongoing Ngrok mining botnet campaign is targeting servers are hosted on popular cloud platforms, including Alibaba Cloud, Azure, and AWS. “ Ngrok Mining Botnet is an active campaign targeting exposed Docker servers in AWS, Azure, and other cloud platforms. It has been active for at least two years.”
















Let's personalize your content