Russia-linked Armageddon APT targets Ukrainian state organizations, CERT-UA warns
Security Affairs
APRIL 5, 2022
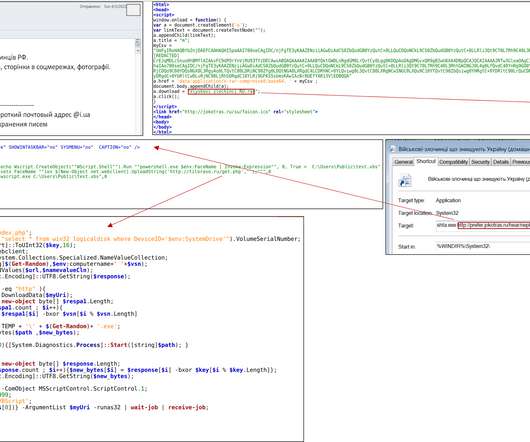
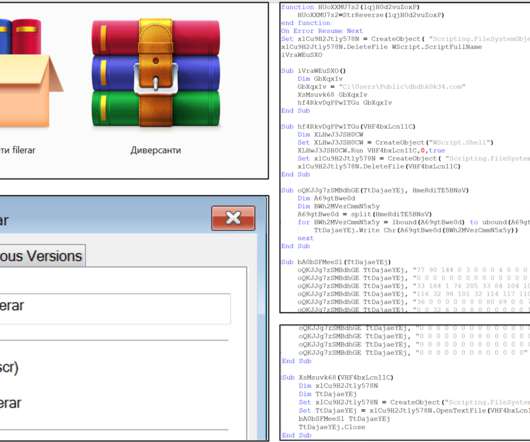
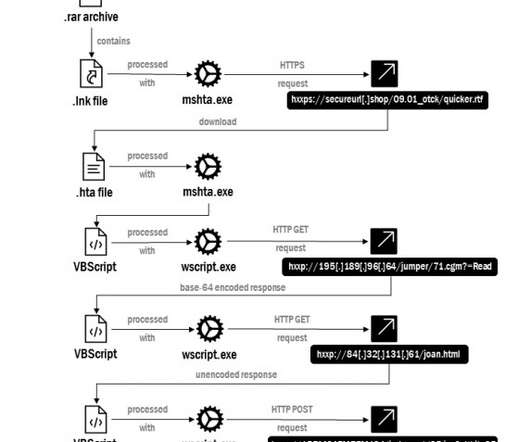
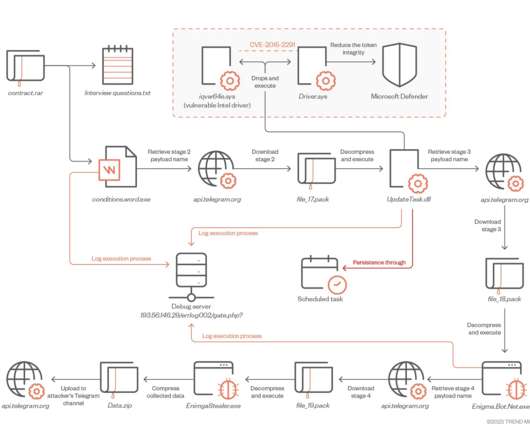
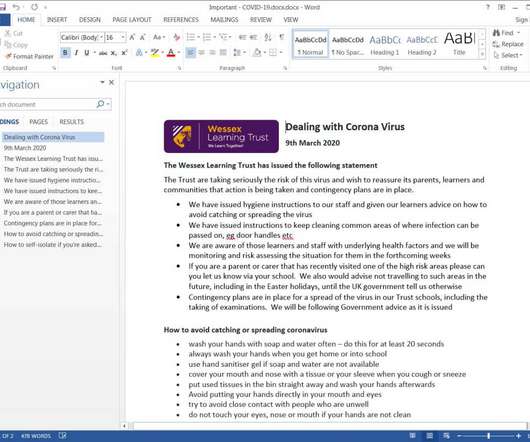
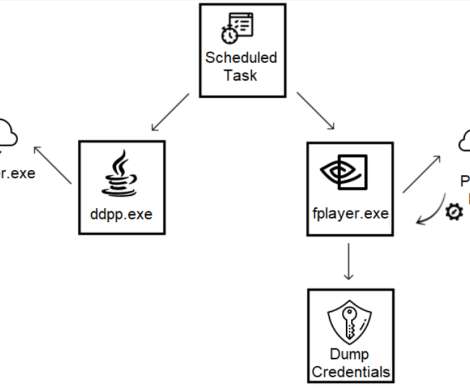
Ukraine CERT-UA spotted a spear-phishing campaign conducted by Russia-linked Armageddon APT targeting local state organizations. The phishing messages have been sent from “vadim_melnik88@i[.]ua,” The messages use the HTML-file “War criminals of the Russian Federation.htm” as attachment.
















Let's personalize your content