European rulings on the use of Google Analytics and how it may affect your business
Data Protection Report
FEBRUARY 14, 2022
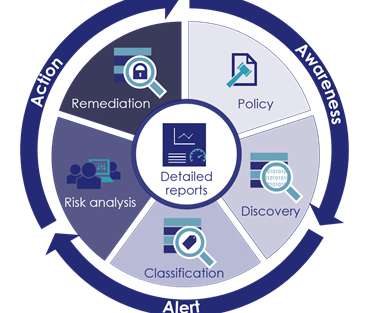
It is important to remember that the analysis should not end with just cookies and Google Analytics. Therefore, it is important to conduct a technical analysis to determine if and how a website or app utilizes these types of services to determine if mitigations are needed. An Important Reminder.













Let's personalize your content