Ransomware Groups Turn to Intermittent Encryption to Speed Attack Times
eSecurity Planet
SEPTEMBER 22, 2022
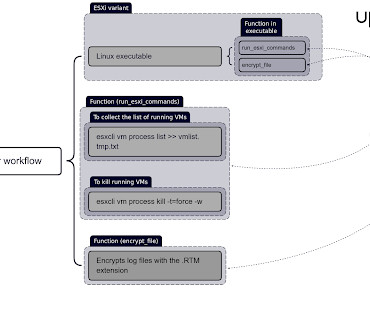
To accelerate the ransomware encryption process and make it harder to detect, cybercriminal groups have begun using a new technique: intermittent encryption. Intermittent encryption allows the ransomware encryption malware to encrypt files partially or only encrypt parts of the files.












Let's personalize your content