Experts warn of a spike in May and June of 8Base ransomware attacks
Security Affairs
JUNE 28, 2023
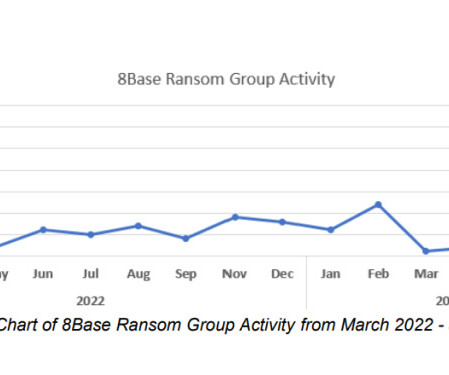
The group has been active since March 2022, it focused on small and medium-size businesses in multiple industries, including finance, manufacturing, business services, and IT. “New analysis from NCC Group’s Global Threat Intelligence team has revealed that ransomware attacks are soaring, with 436 victims in May. .













Let's personalize your content