LockFile Ransomware uses a new intermittent encryption technique
Security Affairs
AUGUST 31, 2021
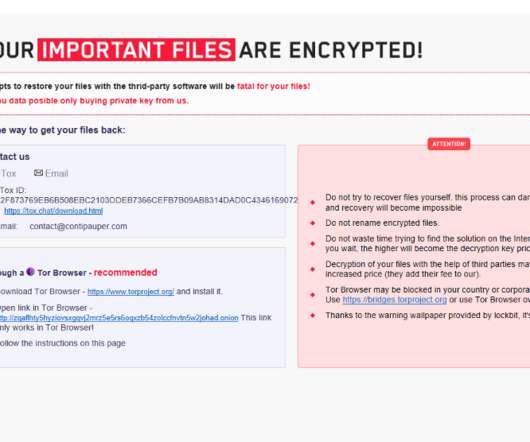
This trick can be successful against ransomware detection software that relies on inspecting content using statistical analysis to detect encryption.” ransomware: The victims of the Lockfile ransomware gang are in the manufacturing, financial services, engineering, legal, business services, and travel and tourism sectors.











Let's personalize your content