Weakness at the Network Edge: Mandiant Examines 2022’s Zero-Day Exploits
eSecurity Planet
MARCH 27, 2023
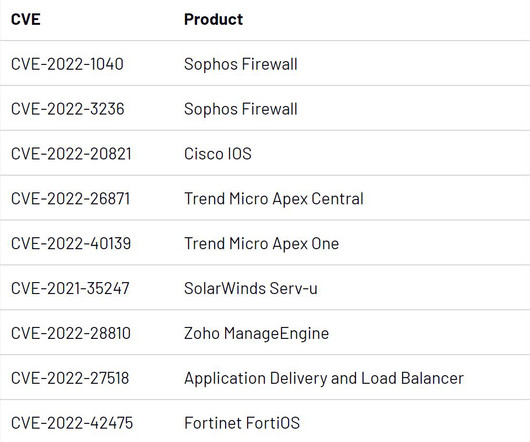
A quarter were financially motivated, and three of those were linked to ransomware operations. Follina , is a vulnerability in Microsoft Diagnostics Tool (MDST), exploited by persuading victims to open Word documents, which can enable the attacker to execute arbitrary code.










Let's personalize your content