TeamTNT group adds new detection evasion tool to its Linux miner
Security Affairs
JANUARY 28, 2021
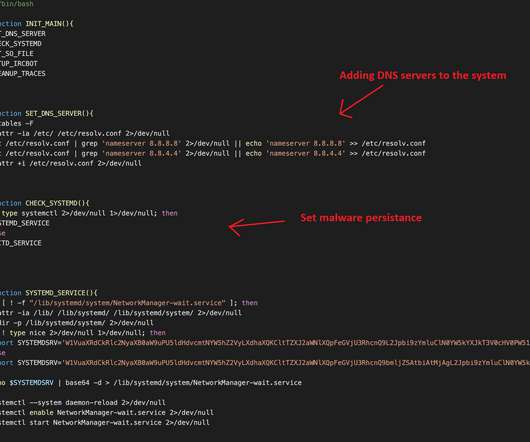
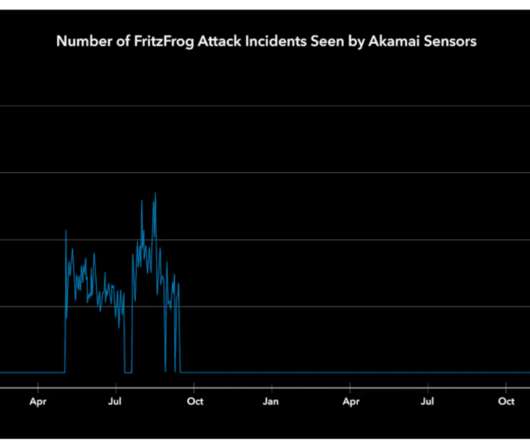
The TeamTNT botnet is a crypto-mining malware operation that has been active since April 2020 and that targets Docker installs. If the custom shared library exports a function with the same signature of a library that is located in the system libraries, the custom version will override it. Pierluigi Paganini.












Let's personalize your content