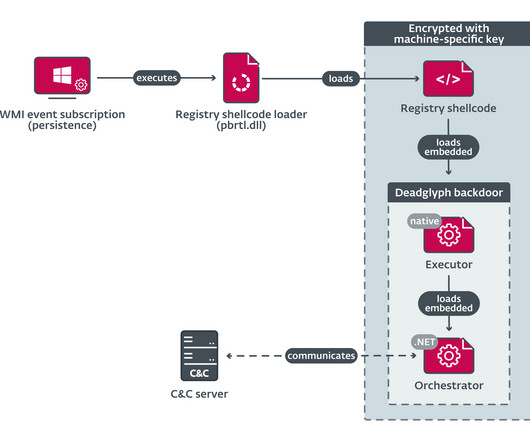
Deadglyph, a very sophisticated and unknown backdoor targets the Middle East
Security Affairs
SEPTEMBER 24, 2023
Stealth Falcon is a nation-state actor active since at least 2012, the group targeted political activists and journalists in the Middle East in past campaigns. The attacks have been conducted from 2012 until 2106, against Emirati journalists, activists, and dissidents. .” ” reads the analysis published by ESET.

















Let's personalize your content