NK-linked InkySquid APT leverages IE exploits in recent attacks
Security Affairs
AUGUST 18, 2021
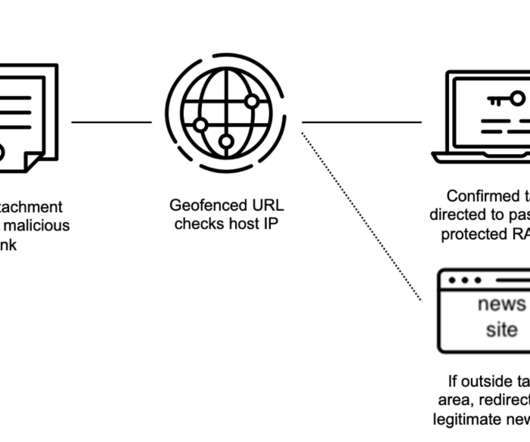
Experts from cybersecurity firm Volexity reported that North Korea-linked InkySquid group (aka ScarCruft , APT37 , Group123 , and Reaper ) leverages two Internet Explorer exploits to deliver a custom backdoor in watering hole attacks aimed at the Daily NK South Korean online newspaper (www.dailynk[.]com). services. . Uninstall the implant.











Let's personalize your content