A Data Security Nightmare Before Christmas
Thales Cloud Protection & Licensing
DECEMBER 13, 2021
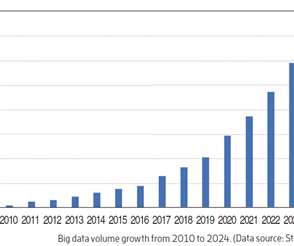
A Data Security Nightmare Before Christmas. Tue, 12/14/2021 - 05:11. Bad people and governments wanted to get their hands on anyone and everyone’s data for their own nefarious purposes. Data Sources: Volume of data/information created, captured, copied, and consumed worldwide from 2010 to 2025 , Statistica.














Let's personalize your content