Who’s Behind the ‘Web Listings’ Mail Scam?
Krebs on Security
MARCH 23, 2020
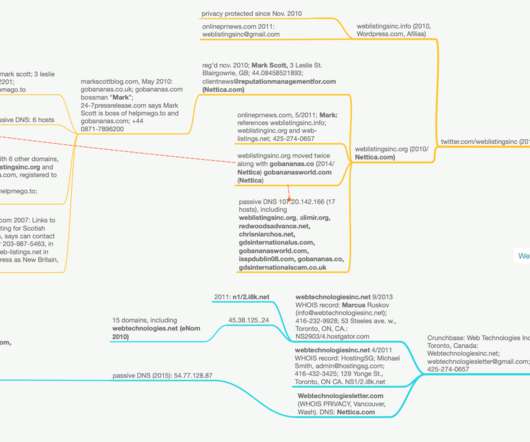
In December 2018, KrebsOnSecurity looked at how dozens of U.S. has posts dating back to 2010, and points to even more Web Listings domains, including weblistingsinc.org. 2010 to a Mark Scott in Blairgowrie, Scotland, using the email address clientnews@reputationmanagementfor.com. Image: Better Business Bureau.













Let's personalize your content