PRIVATELOG, a new malware that leverages Common Log File System (CLFS) to avoid detection
Security Affairs
SEPTEMBER 3, 2021
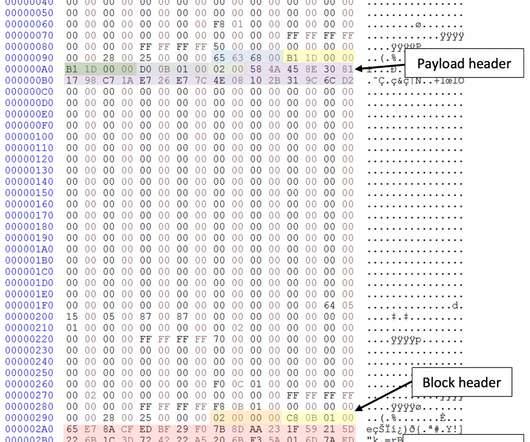
It was introduced with Windows Server 2003 R2 and included in later Windows operating systems. ” reads the analysis published by Mandiant. “Rules to detect CLFS containers matching PRIVATELOG structures or containing encrypted data are also provided. ” concludes Mandiant.






















Let's personalize your content